DevOps Security – Automation and Continuous Security
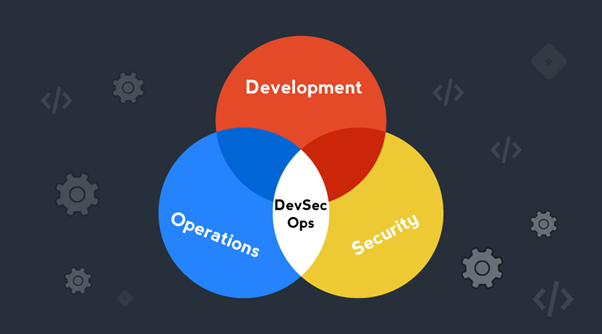
What is DevSecOps?
DevSecOps is the practice of implementing security at every step in DevOps Lifecycle. DevSecOps is based on the concept of integrating security assessments and vulnerability tests at each point of the CI/CD pipeline. DevSecOps implements security within the DevOps workflow. Security is an integral and essential element of DevOps, a method by which enterprises innovate at speed and scale.
What drives DevSecOps?
Business must be become an agile and innovate software delivery machine in order to survive. As software continues to grow at rapid pace, DevSecOps becomes the foundation of competitiveness in modern market. Developers often use and download vulnerable open-source components and applications frameworks. In the DevOps world organizations are building applications at such a faster rate that they have forgotten the Security aspect. Cloud platforms and continuous delivery life cycles often circumvent traditional security process and checks. Security collaboration is everyone’s responsibility.

DevOps security or DevSecOps is a community-driven effort in the standard security world.
DevSecOps focuses on building secure software by implementing security standards at each and every part of the DevOps pipeline from developing to the source code till deploying the application. Whereas standard security practices start after the deploying of the application.
Approach of an organization with DevSecOps is to make each and every person responsible for the software delivery to implement their own security practices. DevOps Security focuses on the point of delivering secure software using continuous delivery architectures. It is community driven effort and strategy driven by learning and experiments.
How Does DevSecOps Work?
The benefits of DevSecOps are simple – Enhanced automation throughout the software delivery pipeline eliminates mistakes and reduces attacks and downtime.
Let’s take a look at a typical DevOps and DevSecOps workflow:
- A developer creates code within a version control management system.
- The changes are committed to the version control management system.
- Another developer retrieves the code from the version control management system and carries out analysis of the static code to identify any security defects or bugs in code quality.
- An environment is then created, using an infrastructure-as-code tool, such as Chef. The application is deployed and security configurations are applied to the system.
- A test automation suite is then executed against the newly deployed application, including back-end, UI, integration, security tests and API.
- If the application passes these tests, it is deployed to a production environment.
- This new production environment is monitored continuously to identify any active security threats to the system.
With a test-driven development environment in place and automated testing and continuous integration part of the workflow, organizations can work seamlessly and quickly towards a shared goal of increased code quality and enhanced security and compliance.
Security Tools
To implement DevSecOps, organizations should consider a variety of application security testing (AST) tools to integrate into their CI/CD process. Some commonly used AST tools follow:
- Static application security testing (SAST)
SAST tools scan proprietary code, or custom code, for coding errors and design flaws that could lead to exploitable weaknesses. SAST tools are used primarily during the code, build, and development phases.
- Software composition analysis (SCA)
SCA tools scan source code and binaries to identify known vulnerabilities in open source and third-party components. They also provide insight into security and license risks to accelerate prioritization and remediation efforts. In addition, they can be integrated into a CI/CD process to continuously detect new open source vulnerabilities, from build integration to pre-production release.
- Interactive application security testing (IAST)
IAST tools, analyse web application runtime behaviour. It detects runtime vulnerabilities and automatically replays and tests the findings, providing detailed insights to developers down to the line of code where they occur. This enables developers to focus their time and effort on critical vulnerabilities.
- Dynamic application security testing (DAST)
DAST is an automated black box testing technology that mimics how a hacker would interact with your web application or API. It tests applications over a network connection and by examining the client-side rendering of the application. DAST tools do not require access to your source code or customization to scan your stack. They interact with your website and find vulnerabilities with a low rate of false positives.
OWASP DevSecOps
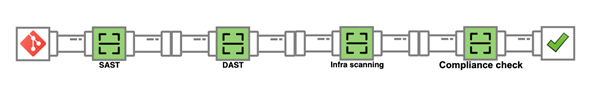
The OWASP DevSecOps focuses on explaining how we can implement a secure pipeline and using best practices and introduce tools that we can use in this matter. This also promotes the shift-left security culture in our development process.
At first, we consider to implement the following steps in a basic pipeline:
- Take care secrets and credentials in git repositories
- SAST (Static Application Security Test)
- DAST (Dynamic Application Security Test)
- Infrastructure scanning
- Compliance check
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting XSS
- Insecure Deserialization
- Using Components with Known vulnerability
- Insufficient Logging and Monitoring

